Taproot is groundbreaking because it’s the first upgrade to Bitcoin in four years.
It was approved by the cohort of Bitcoin miners in early June of 2021 and went into effect the following November. The upgrade means greater transaction privacy and efficiency, and most importantly, the potential for smart contracts. With this article, we’ll discuss what Taproot is and what its implications are for Bitcoin, its users, and investors.
What Does Taproot Do for Bitcoin?
Finally, with Taproot, Bitcoin is compatible with basic smart contract functionality. This is due to two overarching back-end code changes. Specifically, a change in the network’s cryptography method and new support for Merkelized Alternative Syntax Tree (MAST) script execution (we will go deeper into this below).
Because of the complexity of these improvements, and with many investors lacking in-depth knowledge of blockchain, Bitcoin’s price will not readily take into account these upgrades. For all investors, it’s still vital to understand Taproot.
The Upgrades in Detail
Bitcoin’s blockchain network carries as its main function a direct peer-to-peer payments system for transferring value. Our cryptocurrency layering article discussed Layer 2 capabilities, like those offered with the Lightning Network.
However, due to a lack of functionality and scalability issues, Dapps and smart contracts cannot be built on the Bitcoin Layer 1 network. Taproot provides a workaround and eliminates Bitcoin’s code limits to increase real-world uses on the network.
Taproot gives app building, combined with increased scale, privacy, transparency, and fungibility. These changes should increase Bitcoin’s adoption worldwide and, with it, its price.

Schnorr Signatures
The most fundamental change Taproot brings to Bitocin is a rehaul of its cryptography method. It previously used an Elliptic Curve Digital Signature Algorithm (ECDSA). Bitcoin’s creator, Satoshi Nakamoto, used ECDSA to produce a public key (i.e., a public ID) from a private key. Supposedly, he chose this method due to its lack of popularity.
ECDSA signatures are, however, vulnerable to exploits such as lattice attacks. Worse still, they cannot be compressed, slowing transaction processing speed and throughput. With Taproot, Bitcoin is shifting to Schnorr signatures.
These can be compressed. They will also improve the privacy of more complex smart contract transactions, while enabling simultaneous signature processing (batched validations).
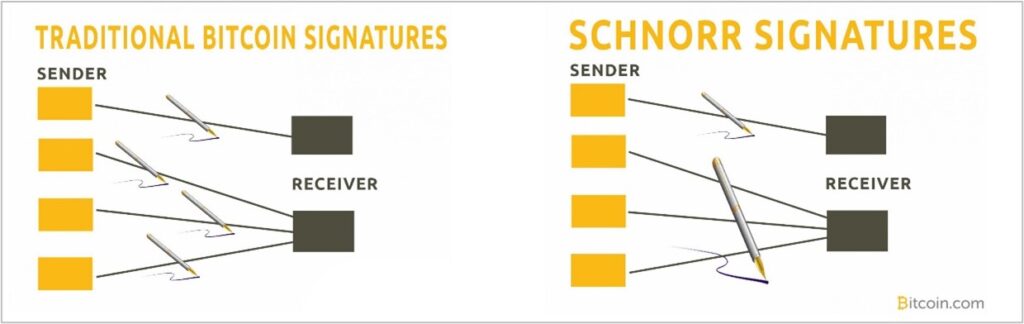
Image courtesy of bitcoin.com
Merkelized Alternative Script Trees (MASTs)
The second change Taproot brings: MAST. These scripts feature a similar function to Schnorr signatures. They minimize on-chain data transfers.
MAST scripts compress transactional conditions into their simplest forms, called Merkle roots. Merkle trees are data structures used in computer science apps. In the case of Bitcoin, Merkle trees encode blockchain data efficiency and securely.
The MAST idea in a nutshell is that you have alternative scripts or script fragments stored as leaves in a single Merkle tree. Those leaves not used can be pruned away, saving space.
Merkle Tree Diagram
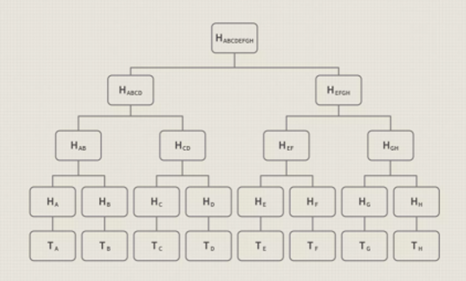
Image courtesy of Investopedia
Compare MAST to P2SH (Pay to Script Hash), where the entirescript must be hashed and then revealed on the blockchain when spent. This brings block space efficiency (and lower transfer costs) and numerous privacy benefits.
With MAST, Bitcoin transactions of greater complexity, such as Bitcoin DeFi apps, are compressed into only one hash each. This minimizes memory usage and increases scalability. MAST enables Bitcoin developers to write more complex scripts requiring less gas (less usage for processing) .
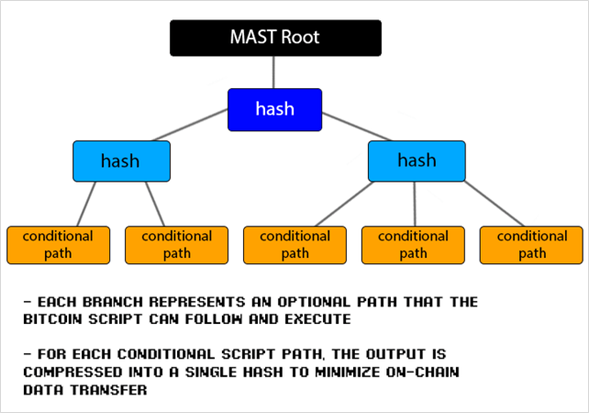
Image courtesy of Stephen Tuttle
The Valuable Combination
Combing Schnorr signatures with MASTs is significant. Taproot means that Bitcoin now has a value beyond a simple Store-of-Value (SoV), like with gold. Bitcoin’s network now has the capability to develop an ecosystem of applications like Ethereum.
As Ethereum continues to grow and accommodate more complex apps, Bitcoins and its players understand the need to compete.
Bitcoin’s Possibilities
For an investor to feel secure with Bitcoin as a portfolio constituent, it’s crucial to understand the possibilities for development that will result from Taproot’s code changes. This understanding requires some technical knowledge, but this relatively simple understanding will still surpass that of the typical investor.
Lightning Network’s Improvements
Our Bitcoin layers article introduced the Bitcoin Lightning Network, a Layer 2 solution that takes Layer 1 bundles and deals with them off-chain, providing Bitcoin with enhanced functionality. This is how Bitcoin has been able to have smart contract functionality in the past.
With Taproot, Lightning Network nodes which minimize memory usage and gas fees of Bitcoin payments by computing the transactions off-chain, shall gain scalability and privacy improvements. The two technical reasons for these improvements are due to Schnorr signatures:
- Switching to point-locked contracts
- Batched validation
These improvements should make Lightning Networks more intuitive and cost-effective for their users.
Lightning Network Applications
With Taproot’s upgrade increasing the efficiency of the Lightning Network, it will also provide for additional development of applications on the Lightning Network. This is an ecosystem of dApps intend to expand the uses for Bitcoin.
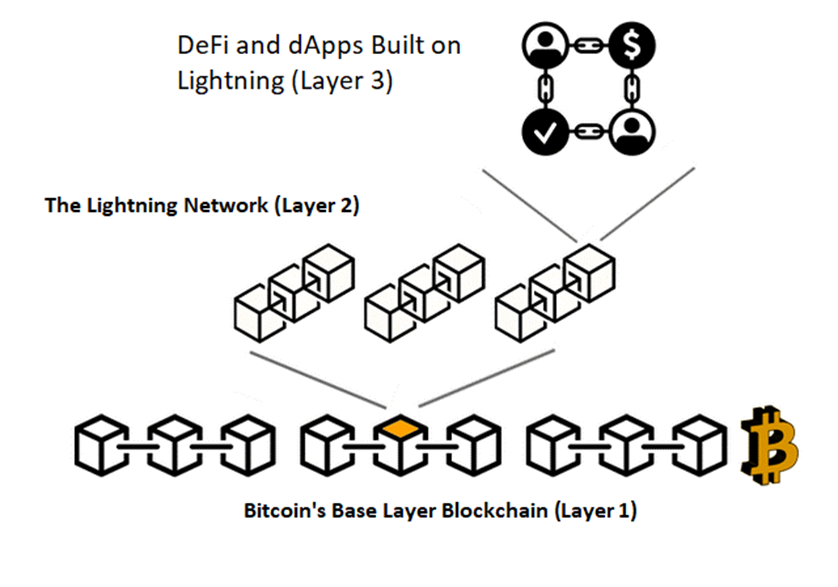
Besides Blockchain developers, few people are aware of Bitcoin’s improved functionality. The primary source network of smart contracts and DApps has been Ethereum.
With “Layers,” we learned that Bitcoin’s Base Layer uses its Proof-of-Work consensus mechanism, Lightning is the Layer 2 of Bitcoin, and to it, we can add Layer 3 DeFi (Decentralized Finance) and dApps.
Taproot Risks
There are risks involved when a blockchain of any kind upgrades. Bitcoin, being the world’s most valuable decentralized network, certainly has many eyes on them. Yet this attention is a double-edged sword. It brings both expert hackers wanted to exploit protocol vulnerabilities, as well as brilliant computer scientists working against them.
Though Taproot should make Bitcoin more secure, there are always potential unforeseen errors, whether during or after Taproot’s implementation. The amount one chooses to invest should mirror their confidence in the upgrade.
Bitcoin’s New Core Function
Before Taproot was released, there was a September 13th Bitcoin Core 22 release hat helped prepare the Bitcoin Core for Taproot. A Bitcoin Core decides which blockchain contains the valid transactions. One of the key upgrades to the Core was Multisig, or coins that require signatures from multiple private keys in order to be spent.
Multisig is used for several purposes. For example, it’s used to secure funds from several devices. Even if one device becomes compromised or lost, the coins remain safe and accessible.
Multisig can also share control over funds between several users but requires cooperation (multiple signatures) to spend the coins.
Summary
The list of technical improvements coming to Bitcoin with Taproot is too long for a single article. Beyond Schnorr signatures and MAST scripts, there are discrete log contracts, script-less scripts, ring signature functionality, and other privacy increases.
The important takeaway, however, is that continued development is coming to Bitcoin. Taproot expands on its single use as a SOV and becomes a platform for dApps and DeFi. This change alone completely reimagines Bitcoin by linking it to Layer 2 and 3 solutions, and the future itself.
Disclaimer: The author of this text, Jean Chalopin, is a global business leader with a background encompassing banking, biotech, and entertainment. Mr. Chalopin is Chairman of Deltec International Group, www.deltecbank.com.
The co-author of this text, Robin Trehan, has a bachelor’s degree in economics, a master’s in international business and finance, and an MBA in electronic business. Mr. Trehan is a Senior VP at Deltec International Group, www.deltecbank.com.
The views, thoughts, and opinions expressed in this text are solely the views of the authors, and do not necessarily reflect those of Deltec International Group, its subsidiaries, and/or its employees.